Tested SFTP Desktop Applications for the Advanced Security and Compliance Platform
Overview of Compatible SFTP Desktop Applications and Tested Encryption Modules for Sharetru's Advanced Security & Compliance Platform
Secure File Transfer Protocol (SFTP) is a critical component in the secure transmission of data over networks. To enhance this security, SFTP encryption can be implemented using sophisticated libraries, such as OpenSSL 1.1.1k used by Sharetru, particularly when operated in Federal Information Processing Standards (FIPS) mode. This Knowledge Base article delves into the nuances of using OpenSSL SFTP encryption, emphasizing its operation in FIPS mode and the significance of its NIST certification.
Understanding SFTP Encryption via OpenSSL 1.1.1k in FIPS Mode
SFTP encryption while using Sharetru is provided through OpenSSL 1.1.1k operated in FIPS mode. Ensuring the highest levels of security, SFTP encryption is often implemented using robust libraries. One such implementation is through OpenSSL 1.1.1k, especially when operated in Federal Information Processing Standards (FIPS) mode.
OpenSSL 1.1.1k Overview:
Description:
- OpenSSL is an essential open-source tool for implementing the SSL and TLS protocols, ensuring secure communication over computer networks. Version 1.1.1k, part of the OpenSSL project, brings a host of security fixes and enhancements aimed at bolstering network security.
Features:
- This version stands out due to its improved security measures and functionalities, setting it apart from its predecessors. Some of the key features include enhanced encryption algorithms, better performance, and more robust security protocols.
FIPS Mode Operation
Explanation of FIPS:
- FIPS (Federal Information Processing Standards) are standards set by the United States government for use in cryptographic software. When OpenSSL operates in FIPS mode, it adheres to these stringent standards, ensuring a higher level of security compliance.
Benefits of FIPS Mode:
- Operating in FIPS mode enhances the security and reliability of OpenSSL. It ensures that the cryptographic operations meet the rigorous standards required by government bodies, making it an ideal choice for sensitive and critical data transfers.
NIST Certification Information:
Certificate Overview
- The National Institute of Standards and Technology (NIST) provides certification for cryptographic modules to ensure they meet established standards. This certification is crucial for ensuring the reliability and security of cryptographic implementations.
Importance of NIST Certification
- NIST certification is a hallmark of quality and security in cryptographic modules. It signifies that the software meets rigorous testing standards and is reliable for secure data transmission.
Details of OpenSSL’s NIST Certification
- OpenSSL 1.1.1k has received NIST certification (Certificate #4642), confirming its compliance with federal standards. This certification covers specific cryptographic algorithms and operational environments, ensuring its suitability for various secure data transfer applications.
Host Key Configuration Guidelines
This section outlines the current policies and standards for host key configurations in RHEL 8, particularly focusing on compliance with FIPS 140-2 standards.
Allowed Host Keys
- RSA and ECDSA Host Keys: In the current configuration, only RSA and ECDSA host keys are permitted. This aligns with our commitment to using secure and recognized cryptographic standards.
Current Host Key Details
-
RSA Key Specifications:
- Size: The RSA key in use is 2048-bits in length.
- FIPS 140-2 Compliance: This key size is approved under FIPS 140-2 standards. No changes are required for RHEL 8 systems using this key size.
-
ECDSA Key Specifications:
- Size: The ECDSA key currently employed is 521-bits in length.
- FIPS 140-2 Compliance: This key size meets the requirements set forth by FIPS 140-2. RHEL 8 systems using this key size do not require modifications.
Discontinued Host Keys
- ED25519 Keys:
- Status: Previously supported ED25519 keys have been removed from our configurations.
- Reason: Although ED25519 is approved by NIST as per FIPS 186-5, it has not undergone testing with OpenSSL 1.1.1k. Consequently, it is not approved for use in our systems until further validation is completed.
User Key Policy Guidelines
This section details the accepted standards and requirements for user key configurations. Adhering to these guidelines ensures security compliance and system integrity.
Accepted User Key Types
- Permitted Key Types: Currently, the system only allows RSA and ECDSA keys for user authentication. This is in line with our security protocols and ensures compatibility with our systems.
Specific Requirements for RSA Keys
- RSA Key Sizes:
- Accepted Sizes: RSA keys must be either 2048 or 3072 bits in size.
- Restrictions: Keys of sizes other than 2048 or 3072 bits have not been tested and are not permitted for use. This is to maintain a standardized security posture and to avoid potential vulnerabilities associated with untested key sizes.
Pending Clarifications
- Investigation into 4096-bit RSA Keys: There is an ongoing evaluation to determine if RSA user keys of 4096 bits can be authenticated and integrated securely. This assessment is part of our continuous effort to update and enhance our security measures.
Supported Cryptographic Protocols
This section outlines the supported algorithms and ciphers for key exchange, message encryption, and message authentication codes (MACs) in our system. These protocols ensure secure and efficient communication during sessions.
Key Exchange Algorithms
Key exchange algorithms are crucial for establishing a secure communication channel. The following algorithms are supported for session key exchange:
-
ECDH (Elliptic Curve Diffie-Hellman) Algorithms:
- ecdh-sha2-nistp521
- ecdh-sha2-nistp384
- ecdh-sha2-nistp256
- Diffie-Hellman Group Algorithms:
- diffie-hellman-group18-sha512
- diffie-hellman-group16-sha512
- diffie-hellman-group14-sha256
- diffie-hellman-group-exchange-sha256
Message Encryption Ciphers
For message encryption, the Sharetru's platform supports a range of ciphers to ensure the confidentiality of data. Supported ciphers include:
- AES (Advanced Encryption Standard) Ciphers:
- aes-256-ctr
- aes-128-ctr
- aes-128-gcm
- aes-256-gcm
MAC Algorithms
Message Authentication Codes (MACs) are used for verifying the integrity and authenticity of a message. The following MAC algorithms are supported:
- HMAC (Hash-Based Message Authentication Code) Algorithms:
- hmac-sha2-512
- hmac-sha2-512-etm@openssh.com
- hmac-sha2-256
- hmac-sha2-256-etm@openssh.com
- hmac-sha1
- hmac-sha1-etm@openssh.com
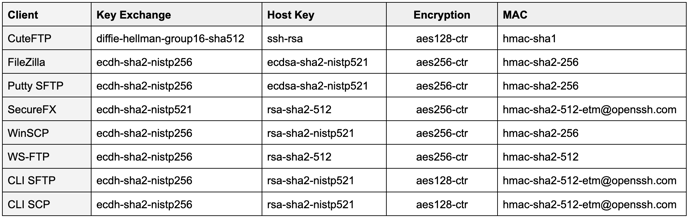
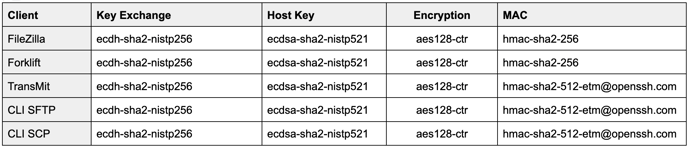
Tested and Verified File Transfer Clients
In this section, we list the file transfer clients that have been rigorously tested and verified to establish proper connections using our system. These clients are confirmed to comply with the standards outlined in the previous sections. If a client is unlisted, you must ensure it meets the standards listed above.
Windows
MacOS
Linux
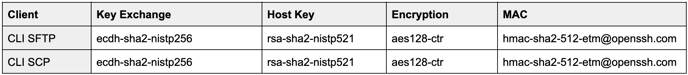
Note: FileZilla does not support FIPS Key Exchange algorithms.
%20Logos%202022/sharetru%20logo%20white%20bg%20and%20padding.png.png?width=300&height=75&name=sharetru%20logo%20white%20bg%20and%20padding.png.png)